You must log in or # to comment.
Please explain if I’m wrong because I think I am because it can’t b this stupid.
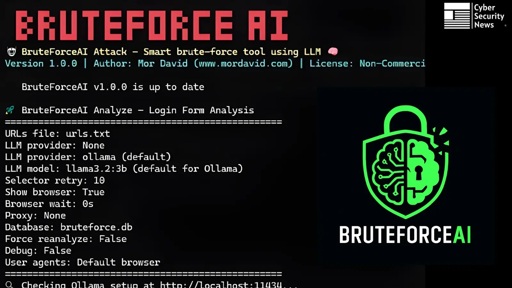
Its using llama to discover the way to enter credentials? And then using a normal brute force attack once that’s done?
Sounds like it. Presumably useful for large corporations and such where there may not be a clear picture of potential entrypoints into the system. You can just let it loose and it’ll find login pages on its own and process them.